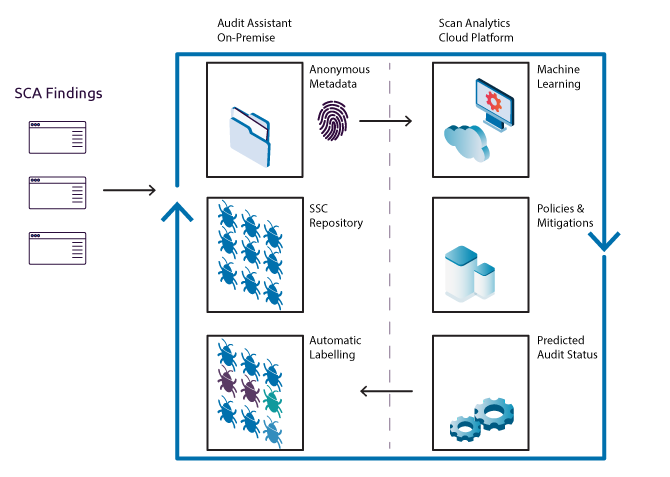
Cookie Policy
Cookies
Cookies are used on this website. By using our website, you agree that cookies are to be placed on your device as further explained below.
Cookies are small pieces of data that a website sends to your computer’s web browser while you are navigating through it. They have many different purposes, but mainly, cookies enable you to navigate between pages easily, to remember your preferences, and eventually to improve the user experience. These cookies may then be stored on your machine to identify your computer.
Cookies used on this website can be either set up by our website or by a third-party website. Moreover, these cookies can be “session” or “persistent” cookies: a session cookie is a cookie that is automatically deleted when the user closes the browser, whereas a persistent cookie is a cookie that remains stored in the user’s terminal device until it reaches a defined expiration date. Cookies used on Sogeti website have a maximum lifetime of 12 months.
A. Types of cookies we use
We use several types of cookies on this website as described below.
Strictly necessary cookies
These cookies are essential to enable you to move around the website and use its features, such as accessing secure areas of the website. Without these cookies, services you have asked for cannot be provided.
Strictly necessary cookies used on the Sogeti website:
- Registered visitor cookies.
Functionality cookies
These cookies allow a website to remember choices you make and provide enhanced, more personal features. For instance, a website may be able to provide you with local information or news by storing in a cookie the region in which you are currently located. These cookies can also be used to remember changes you have made to the text size, font and other parts of the web pages that you can customize. They may also be used to provide services you have asked for such as watching a video or commenting on a blog. These cookies cannot track your browsing activity on other websites. They do not gather any information that could be used for advertising. Functionality cookies used on the Sogeti website:
- Registered visitor functionality cookies.
- Social plug-in content sharing cookies.
Performance cookies
These cookies are used to collect information about how visitors use a website, for instance which pages they go to more often, and if they get error messages from web pages. All information collected by means of these cookies is anonymized, aggregated and only used to develop and track traffic patterns and the volume of use of our website and to improve how our website works. This information is for Sogeti’s exclusive use and is not shared with any third party or connected to any other information.
Performance cookies used on the Sogeti website:
- Unregistered visitor cookies.
- Analytic cookies.
Targeting cookies
These cookies are used to deliver advertisements that are targeted to be relevant to you, limit the number of times you see an advertisement, and help measure the effectiveness of the advertising campaign. They are usually placed by advertising agencies with the website operator’s permission. They remember that you have visited a website and this information is shared with other organizations such as advertisers. Quite often they will be linked to a website functionality provided by the other organization. We do not have third-party advertising on our website. We use targeting cookies only for our own analytic purposes. Third-party social media websites may log certain information (such as your IP address, browser type, language or access time) if you are logged in to those social media websites as you are navigating through our website. They may also link such collected information with your profile information on that website. We do not control these third-party tracking technologies, thus we recommend that you read the terms of use and privacy policy of such websites before using them.
B. Use of cookies
We may use personal data collected from our cookies to identify user behaviour and to serve content and offers based on your profile.
The performance cookies used on this website do not collect personal data. Other cookies can collect personal data (including information from cookies placed via our advertisements on third-party websites):
- If a user is a registered user.
- If we send you a targeted email which includes web beacons, cookies or similar technologies we will know whether you open, read, or delete the message.
- When you click a link in a marketing e-mail you receive from Sogeti, we will also use a cookie to log what pages you view and what content you download from our websites, even if you are not registered at or signed into our site.
Here is a list of the main cookies we use on our website:
| Cookies |
Description |
| Registered visitor cookie |
Cookie given to each registered user. |
| Registered visitor functionality cookie |
Cookies used to remember the unique identifier given to each registered user. |
| Social plug-in content sharing cookie |
Cookies set by services such as Facebook Connect or Twitter Button, which allow social networks users to share the content of our websites on social networks. |
| Unregistered visitor cookie |
Cookies used to give to unregistered users a unique identifier in order to recognize them and to analyze how they use the website. |
| Analytic cookie |
Cookies used to store URLs of the previous page visited, enabling to track users navigating from inside or from outside the website. If you click on a Sogeti advertisement on a non-Sogeti website, a cookie may be used to log which website you are on, in order to ensure our advertisements are served effectively and to measure whether our advertisements are viewed.
- Google Analytics: cookies set by Google analytics are used for web analytical purpose, but are not used to track individual users. For further information on how Google Analytics collects and uses information on our behalf and the right to use such cookies, please refer to the Google Analytics products and services privacy statement. If you object to your Personal Data being collected by Google Analytics, you may download and install the Google Analytics Opt-out Browser Add-on.
- Pardot: cookies set by Pardot are used to track users on our website. Visits are tracked for known users only. Unknown users are recorded as anonymous users. Please refer to Pardot privacy policy for any further information on their use and your rights related to the use of such cookies.
|
C. Other non-cookie technologies:
Sogeti also enables the use of technologies that perform functions similar to cookies such as web beacons or other technologies that may be included in marketing e-mail messages or newsletters in order to determine whether messages have been opened and links clicked on. Web beacons do not place information on your device, but may work in conjunction with cookies to monitor website activity.
D. “Do-not-track” signals
Some web browsers may transmit “do-not-track” signals to the websites with which the browser communicates. As of the Effective Date of this Privacy Policy, an industry standard has not yet been established on how to respond to these signals. Therefore, our website does not currently recognize or respond to these signals, but Sogeti will reassess its response approach once a standard is established. However, at this time you can generally express your privacy preferences regarding the use of most cookies through your web browser.
E. How to accept or refuse cookies
If you do not want to receive cookies from our website, you may set your browser to refuse cookies or to notify you when you receive a cookie, which you may then accept or refuse upon such notice. You can also generally set your browser to turn off cookies. To understand how to do this, please consult your browser’s “Tools” section, or any other similar heading.
We recommend that you leave the cookies active. Bear in mind that if you block, turn off or otherwise reject our cookies, some web pages may not display properly or you will not be able to use any website services that require you to sign in.
If you object to have cookies placed on your machine, you need to disable them. In order to do so, please follow the relevant instructions depending on your browser: